3. Configure Systems Manager Session Manager
As we observed during our initial evaluation, our activity within a session is not yet being logged. In this step, we are going to configure Session Manager to store session log data in a specified Amazon S3 bucket for auditing purposes. The default option is for logs to be sent to an encrypted S3 bucket. Encryption is performed using the key specified for the bucket.
Create a Custom Policy for Amazon S3 Bucket Access
Creating a custom policy for Amazon S3 access is required only if you are using a VPC endpoint or using an S3 bucket of your own in your Systems Manager operations.
-
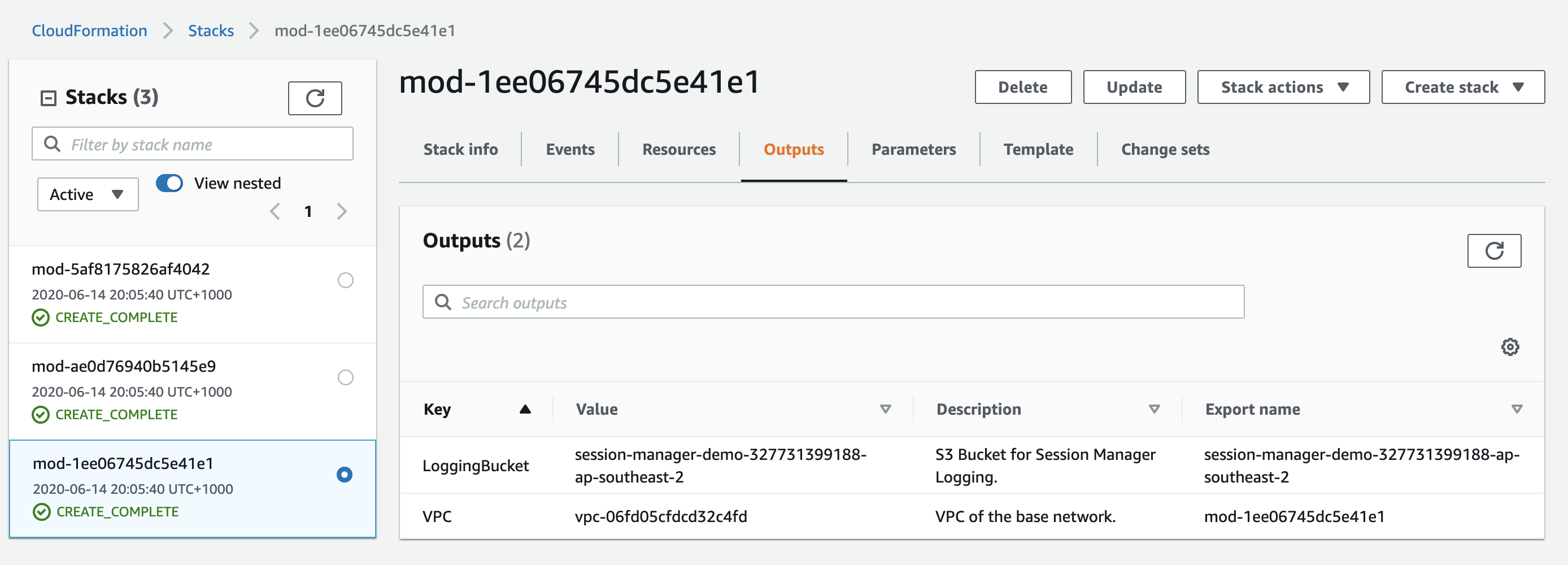
Browse to the CloudFormation console, and select the stack starting with mod- and Description Session Manager workshop. Select the output tab and note down the S3 bucket name with the key value of Logging Bucket. This bucket will follow the naming convention session-manager-demo-[ACCOUNT_NUMBER]-ap-southeast-2 as below.
-
Open the IAM console
-
In the navigation pane, choose Policies, and then choose Create policy.
-
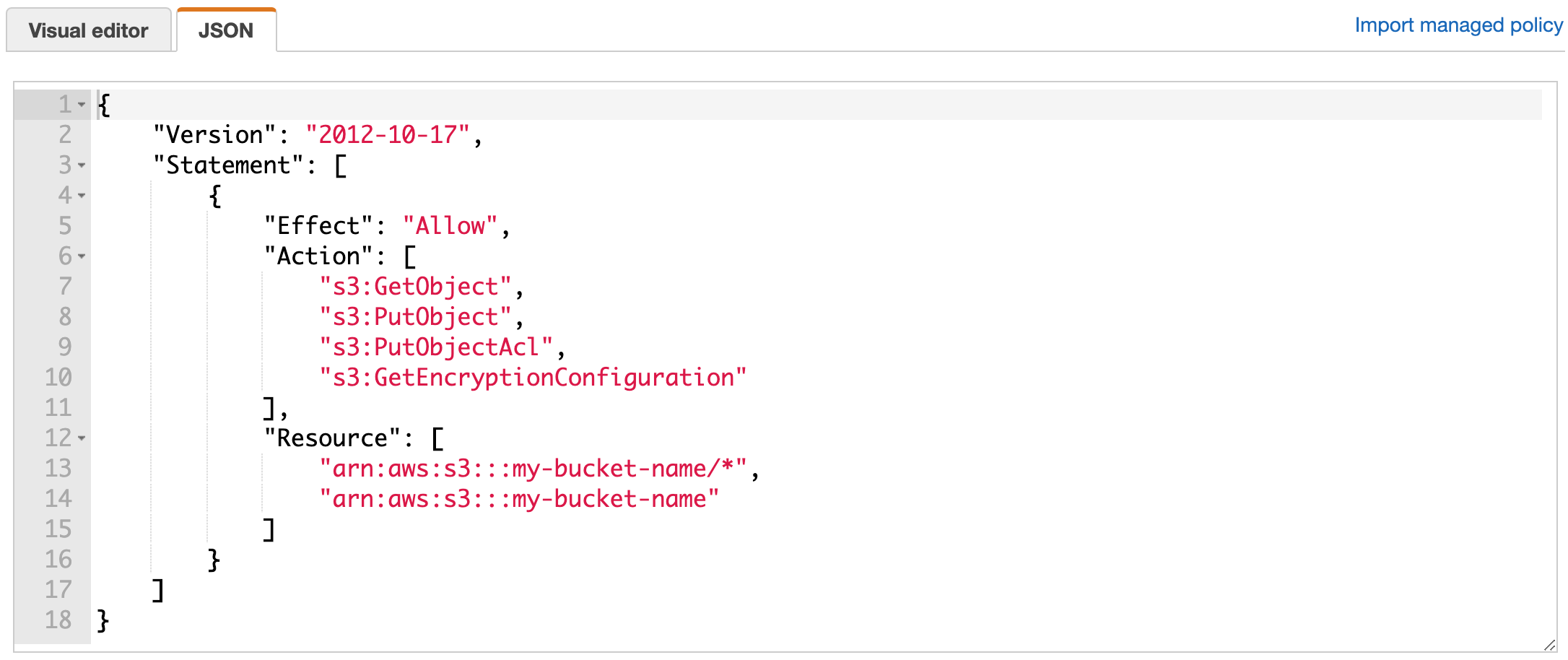
Choose the JSON tab, and replace the default text with the following:
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": [ "s3:GetObject", "s3:PutObject", "s3:PutObjectAcl", "s3:GetEncryptionConfiguration" ], "Resource": [ "arn:aws:s3:::my-bucket-name/*", "arn:aws:s3:::my-bucket-name" ] } ] }Replace
my-bucket-namewith the bucket name from step 1. -
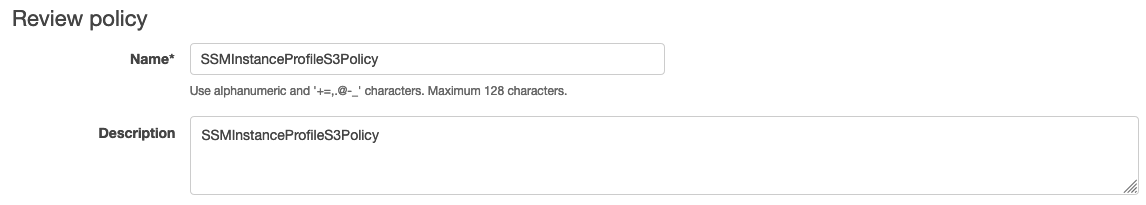
Choose Review policy.
-
For Name, enter a name to identify this policy, such as SSMInstanceProfileS3Policy or another name that you prefer.
-
Choose Create policy.
Attaching Policy to Instance Profile Role
- After the policy has been created, open the IAM console and head into Roles in the navigation menu to the left and search for session-manager-demo-default.
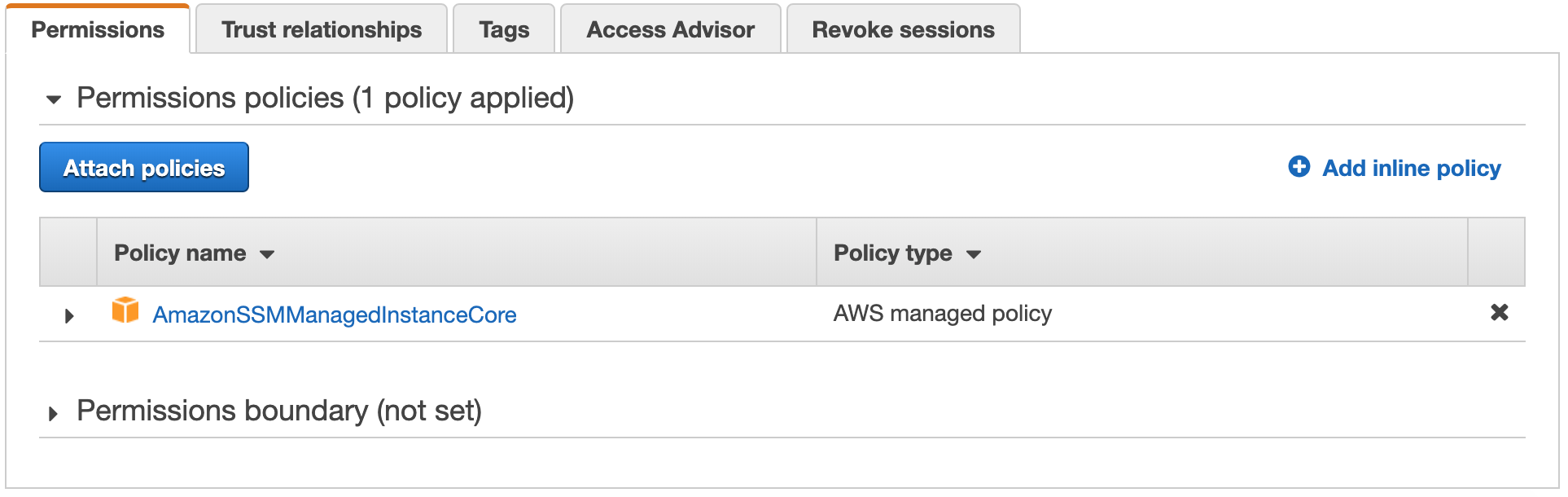
- Then, click on Attach policies.
- In the Filter, enter SSMInstanceProfileS3Policy as the policy to select.
- Select the policy and click on Attach policy.
Enable Session Logging for Session Manager
Once the policy has been created and associated with our Instance Profile, we will configure session logging to the S3 bucket we created using CloudFormation.
-
Under Instances & Nodes in the AWS Systems Manager navigation menu, browse to Session Manager and select Preferences tab and Edit option
-
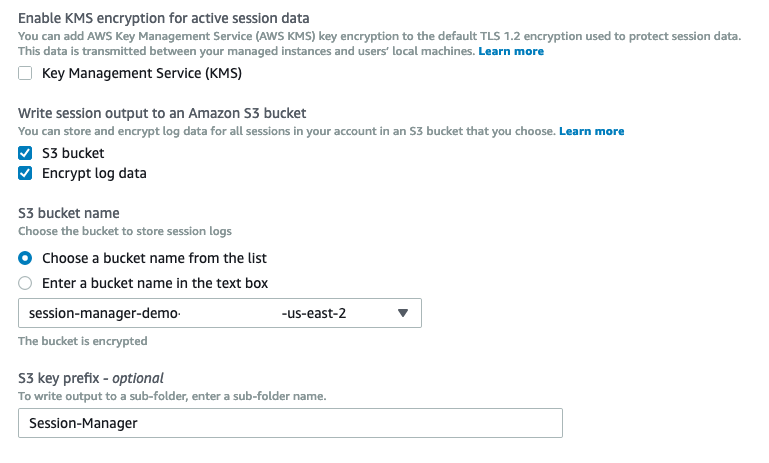
Under the Write session output to an Amazon S3 bucket heading, select S3 bucket.
-
Leave Encrypt log data selected. In the S3 bucket name field, select the bucket you noted down at the start of this step. In the S3 key prefix field, enter Session-Manager. Click Save
-
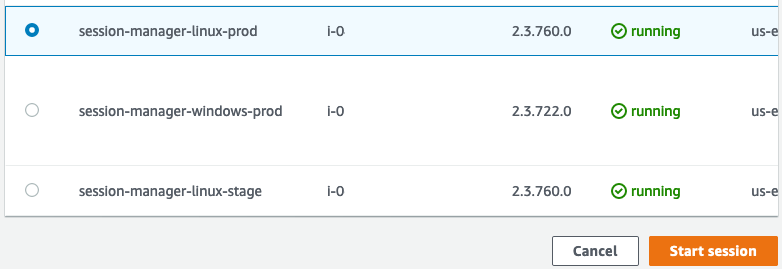
Select the Sessions tab, click Start Session, select a Linux instance and click Start session.
-
Execute some basic commands to demonstrate session logging is working as expected:
ps -ef | grep -i ssmsudo ls -l ../etcwhoamiexitterminate the session.
-
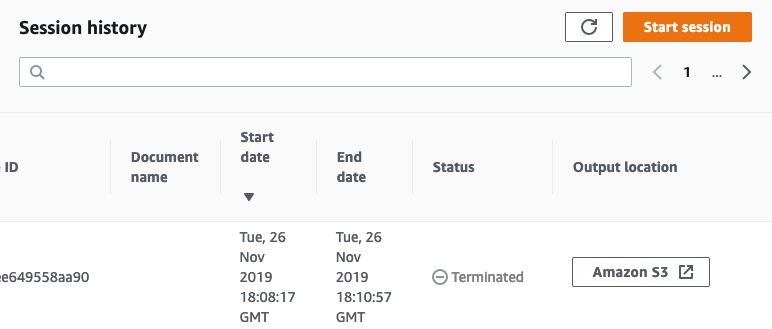
Browse to the Session History tab and locate our last session. Wait for session Status to change from Terminating to Terminated. In the Output location column, click Amazon S3 to view the session log.
-
Observe the data captured in the session log includes all input and output of the commands we entered.
Note: The S3 bucket created for you is configured to use S3 Default Encryption with AWS S3-managed keys (SSE-S3). All session log data will be encrypted by default but you can also choose to use your own KMS Customer Master Key (SSE-KMS).
Stuck? Watch this
This video has no audio