7. AWS Config: Compliance as Code
Create a Config Rule to alert on whether the SSM Agent is working
In this step we will add a config rule to our environment using an AWS Managed rule that will evaluate if EC2 instances in the account have a working AWS Systems Manager Agent.
- Open the AWS Config console.
- Click on Rules in the navigation menu at the left of the console.
- Click on the Add rule button:
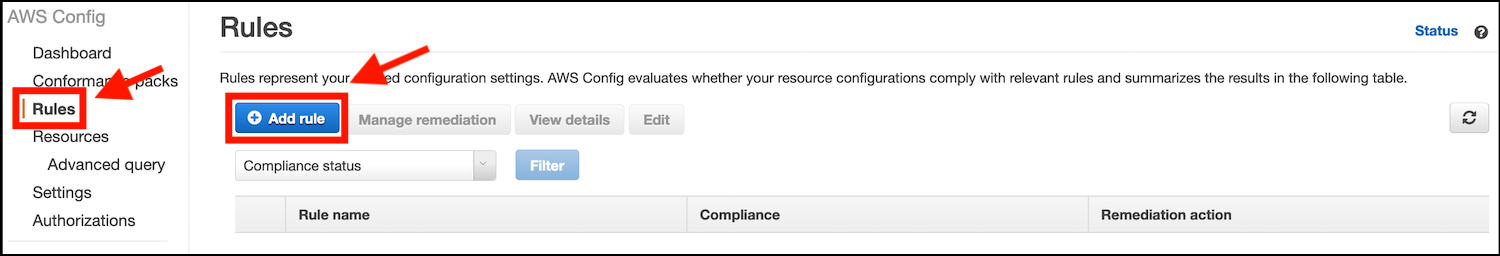
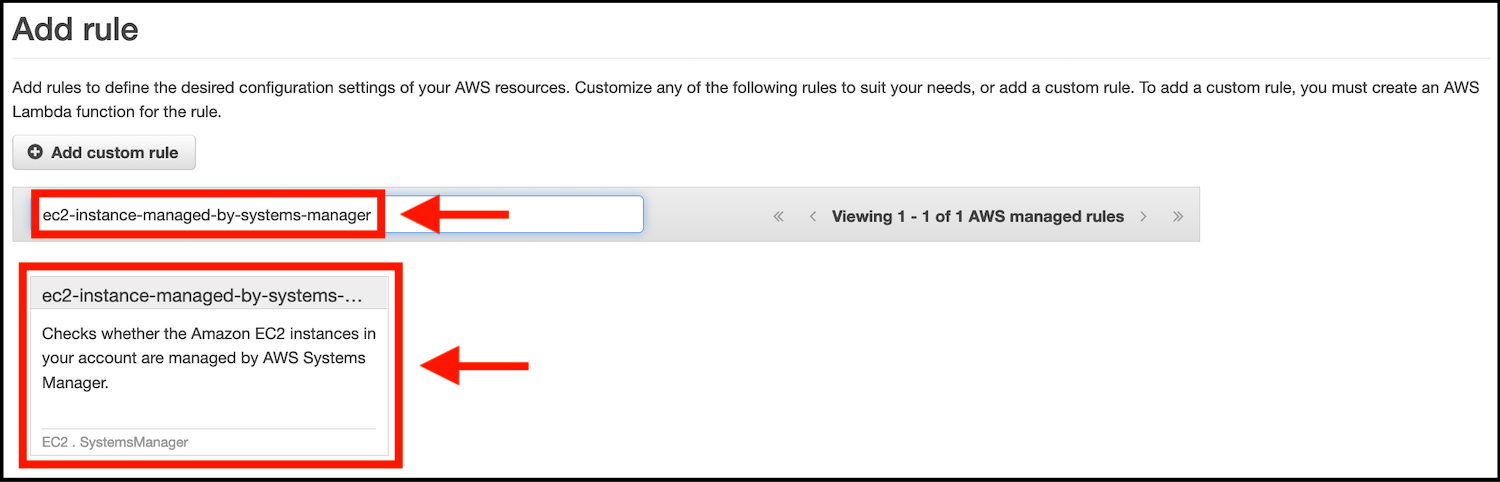
- On the Add Rule screen type ec2-instance-managed-by-systems-manager in the Find by rule name search field. Click on the displayed rule box:
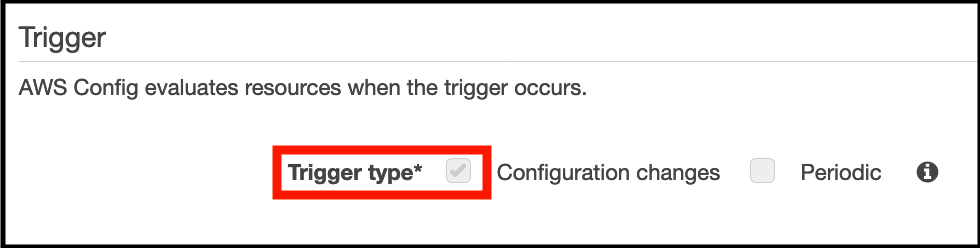
- In the Trigger section take note of the Trigger type (When configuration changes):
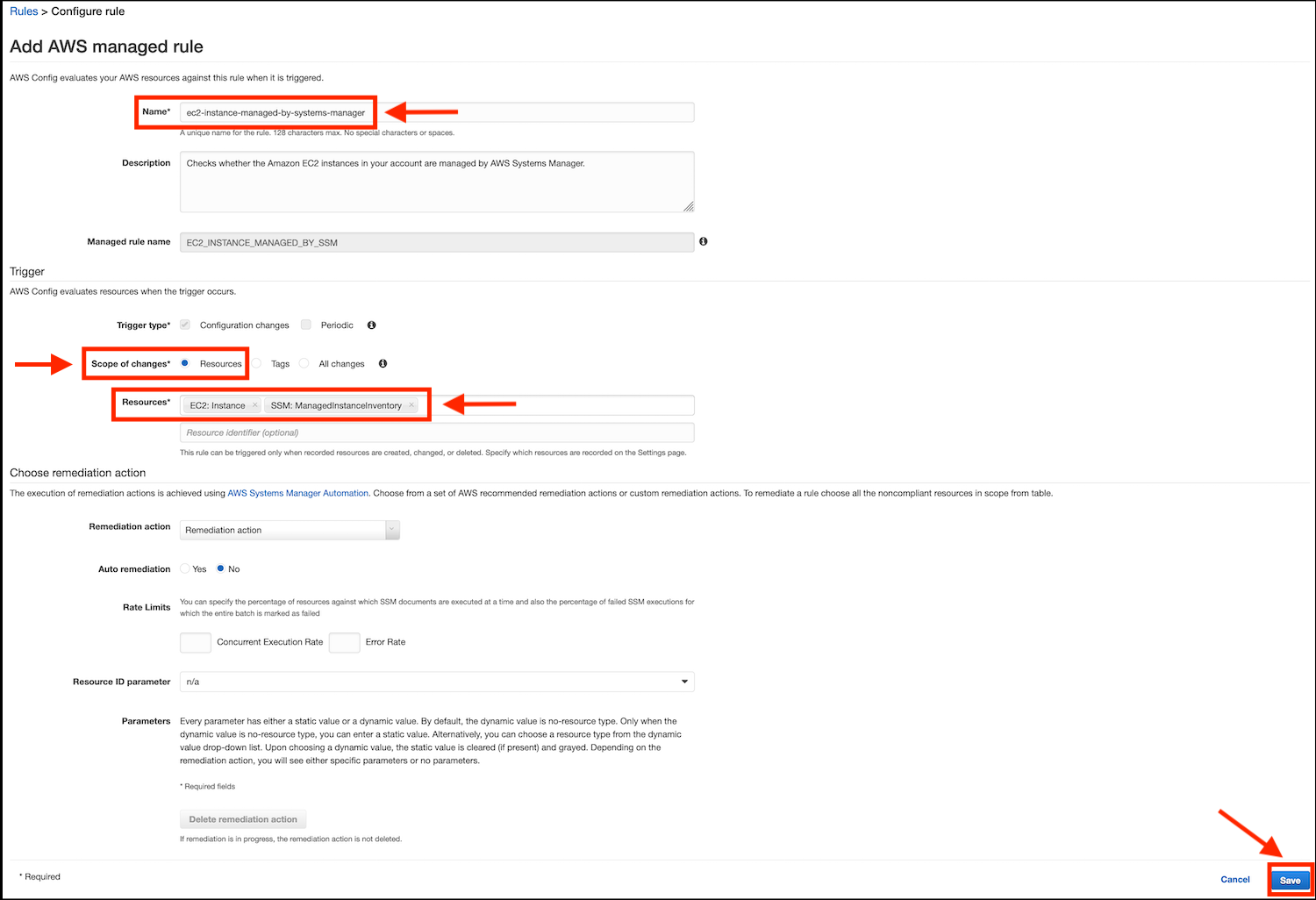
- Leave all other settings on their defaults and click on the Save button.
You can create Config Rules to monitor a number of items within your infrastructure. Besides utilizing AWS managed Config rules you can also create custom rules using Lambda Functions. Located here in Github are some sample Config rules you can create and implement using AWS Lambda.
Test Config Rule by Deploying an EC2 Instance
To test the AWS Config rule we will now deploy a new EC2 instance.
- Open the EC2 console.
- In the navigation menu on the left, click on Instances, under the INSTANCES heading:
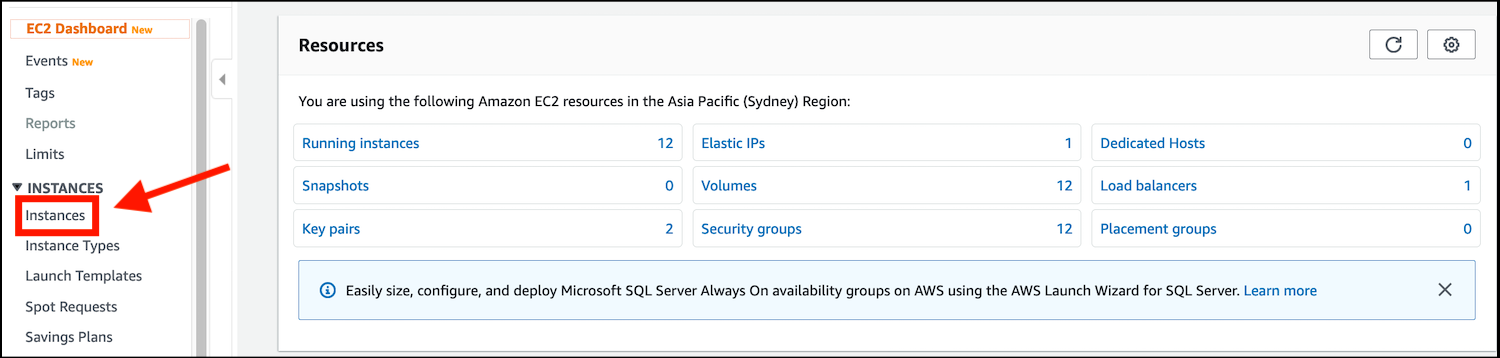
- Click on the Launch Instance button:
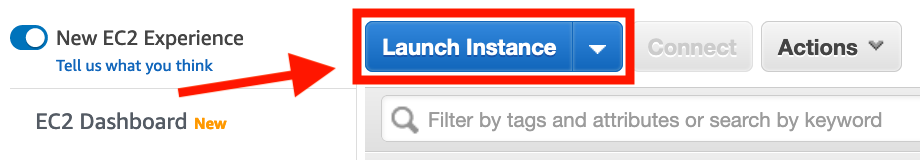
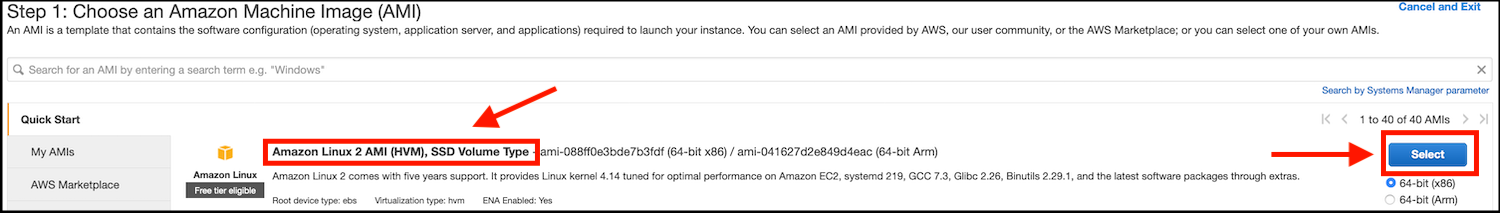
- Choose the first Operating System choice in the list - Amazon Linux 2 AMI (HVM) - by clicking on the Select button next to it:
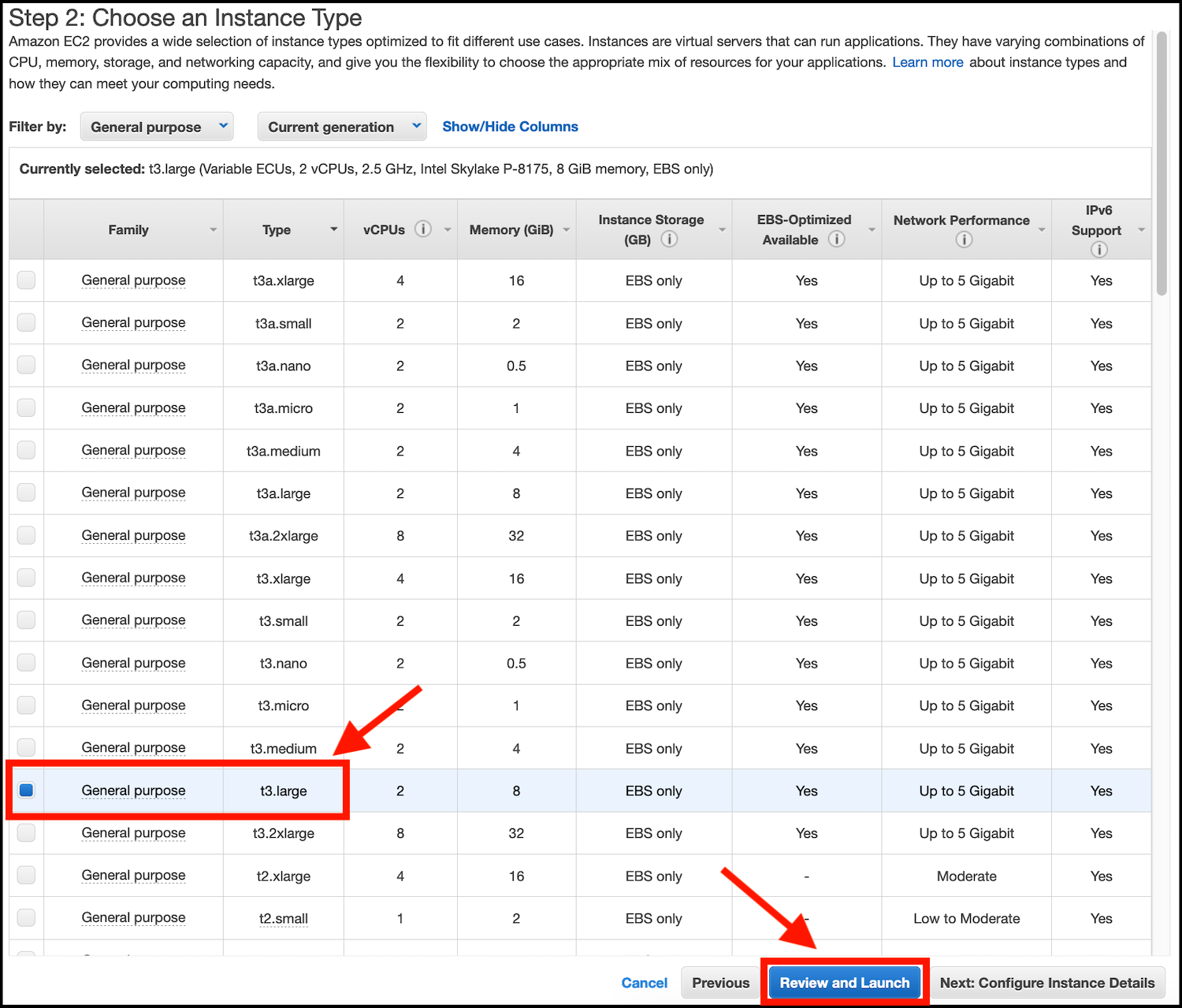
- On the Step 2: Choose an Instance Type screen tick the box next to t3.large, then click on the button Review and Launch:
- On the Review Instance Launch screen click on the Launch button.
- Select the SSMLabKeys key pair and tick the box to acknowledge the warning. Click on the Launch Instances button:
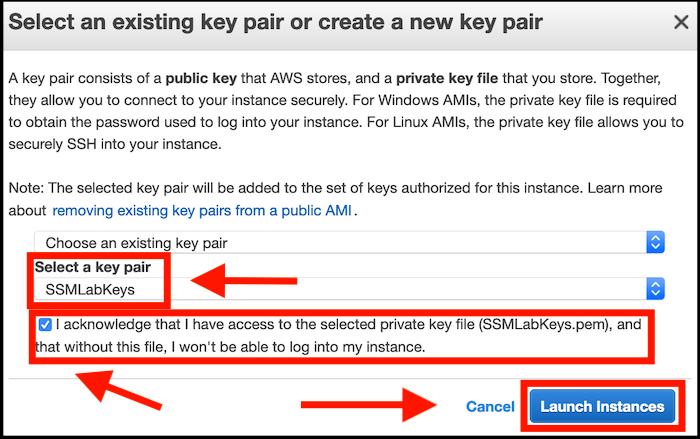
The EC2 instance will now be created for you.
- Click on the view Instances button at the bottom right of the console. Look for the instance that has no name in the Name column (this will be the one you just created). Make a copy of the Instance ID:
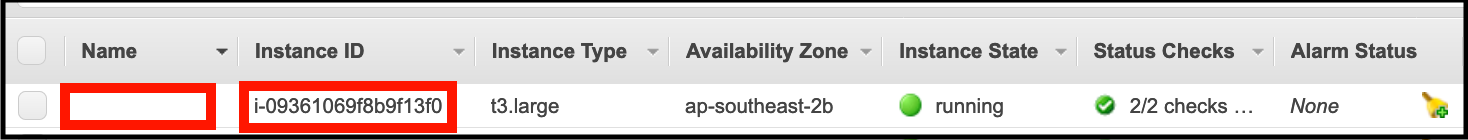
- Open the AWS Config console.
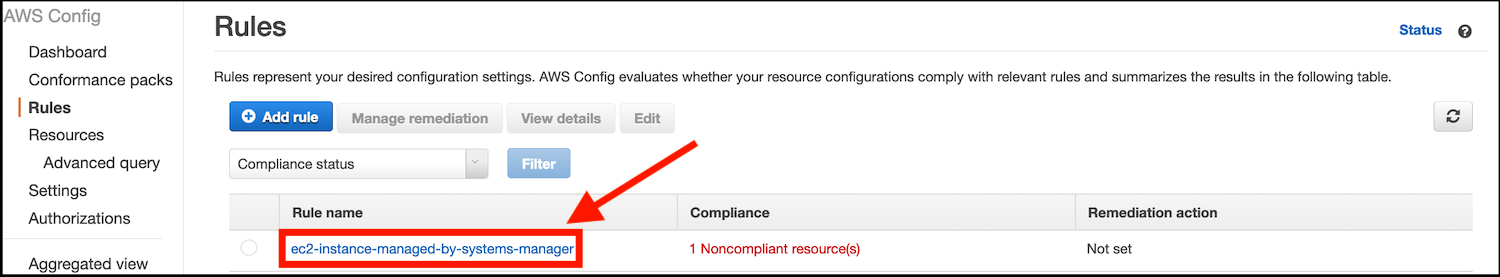
- Click on Rules. The rule you deployed earlier will be shown. click on the rule name (ec2-instance-managed-by-systems-manager):
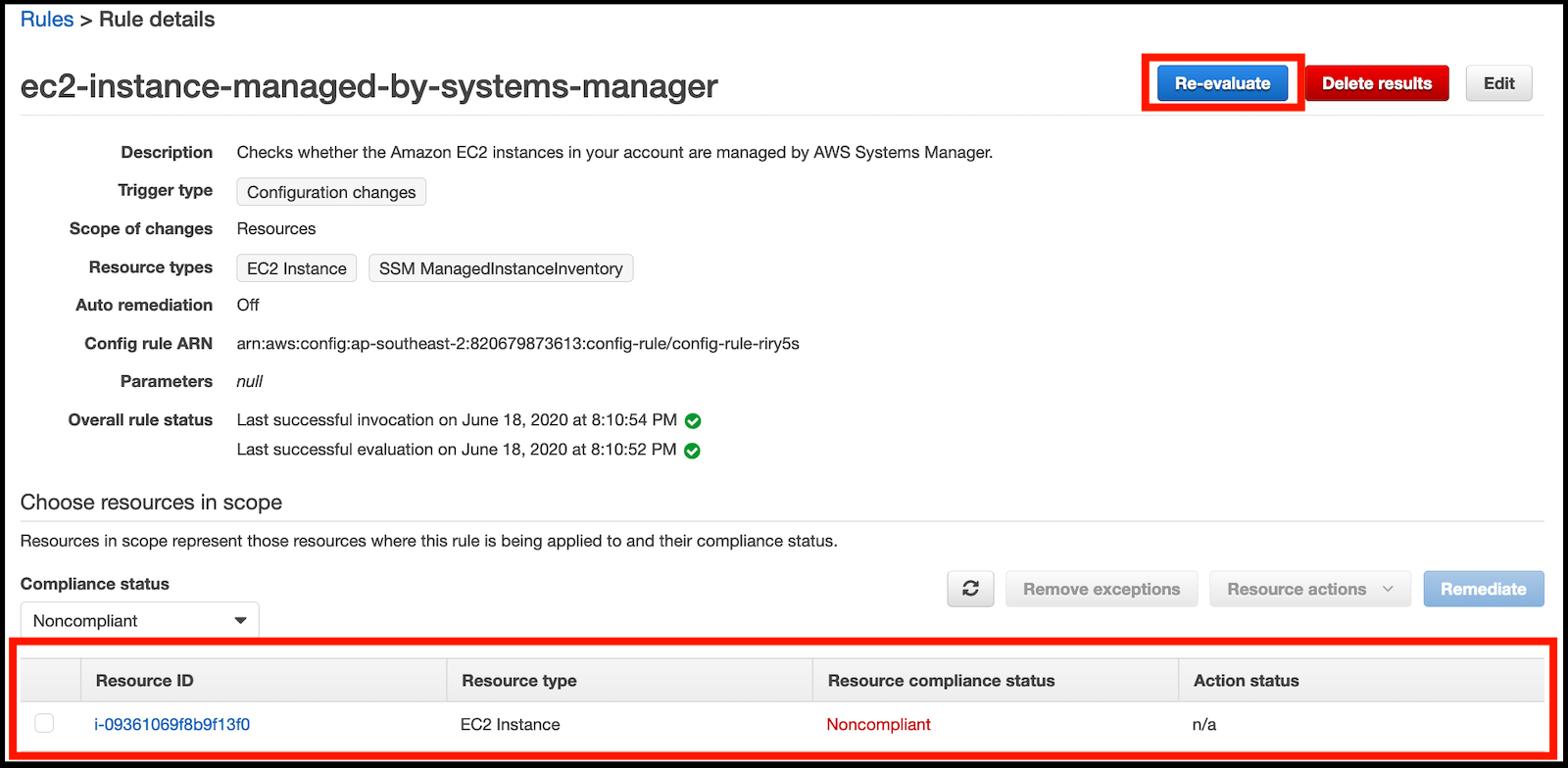
- If the EC2 instance has been deployed and running for several minutes the rule will have updated automatically to add the new EC2 resource that is non-compliant to the list. Look for the Instance ID you noted down in step 8 (If it has not yet updated, click on the Re-evaluate button in the top left of the console, then refresh the web page until the rule flags the EC2 instance as Noncompliant):
- Click on Rules. The rule you deployed earlier will be shown. click on the rule name (ec2-instance-managed-by-systems-manager):
Remediate Non-compliant Resources
Now we will remediate the non-compliant resource:
-
Open the CloudFormation console.
-
Click on the blue stack name ConfigLabStack:
-
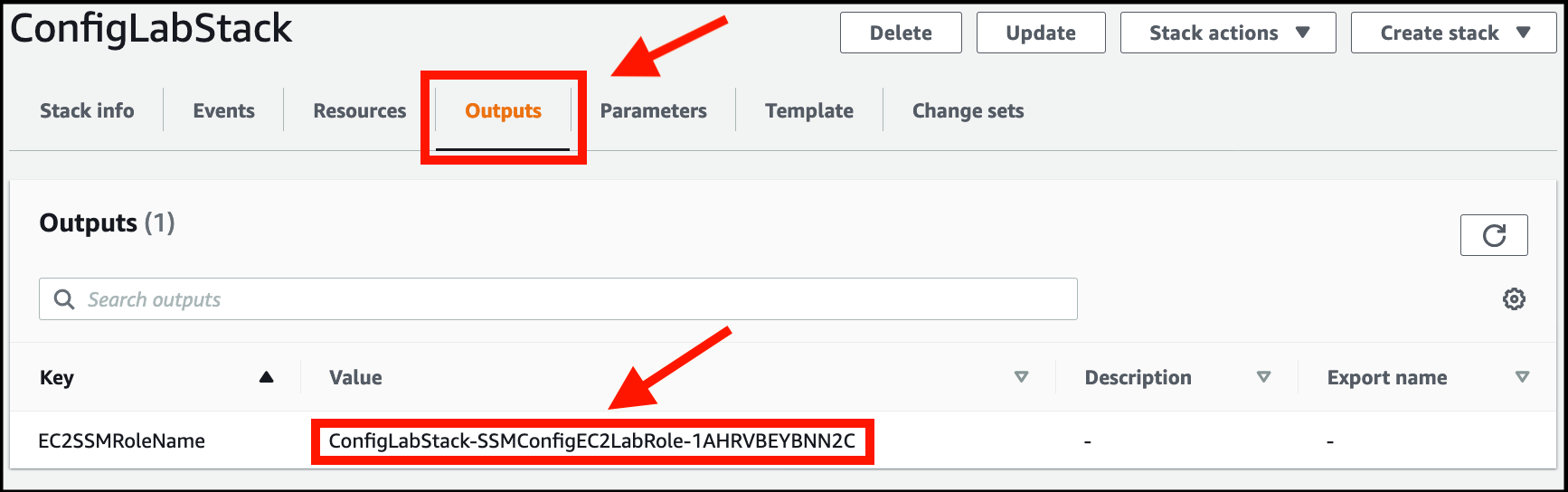
Click on the Outputs tab.
-
Look for the Key called EC2SSMRoleName and copy the Value next to it to a text document (it will look similar to this - ConfigLabStack-SSMConfigEC2LabRole-, with some numbers and characters at the end):
-
Open the AWS Config console.
-
Click on Rules in the navigation menu on the left of the console.
-
Click on the blue rule name ec2-instance-managed-by-systems-manager.
-
Click on the Edit button to edit the ec2-instance-managed-by-systems-manager Config rule:

-
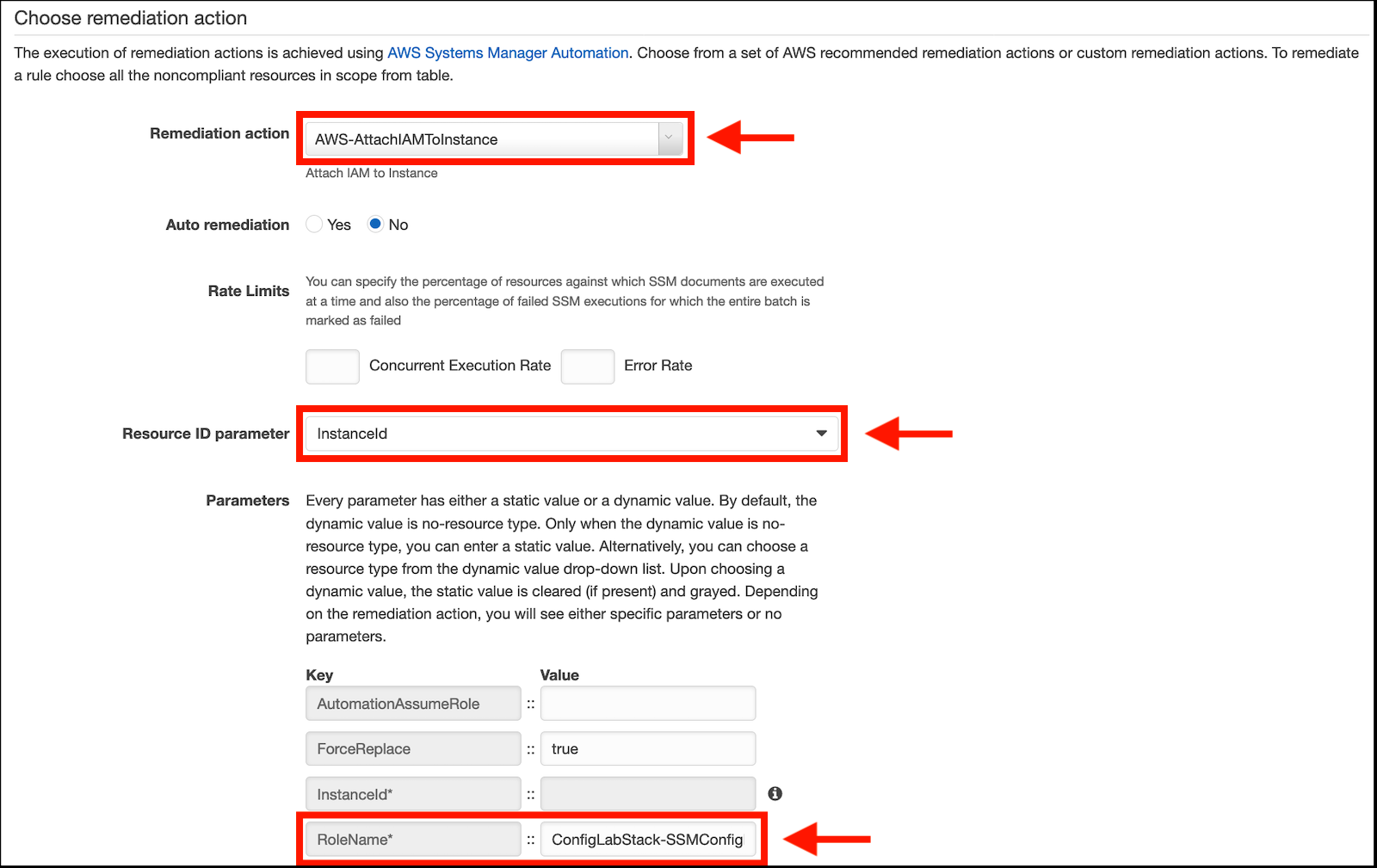
In the Choose Remediation Action section do the following:
- Remediation action: choose AWS-AttachIAMToInstance
- Click on the dropdown selection for Resource ID parameter and choose InstanceId (this will pass the non-compliant Instance ID to the remediation action)
- In the Parameters section paste the value you copied in step 4 into the field next to RoleName
-
Click on the Save button.
-
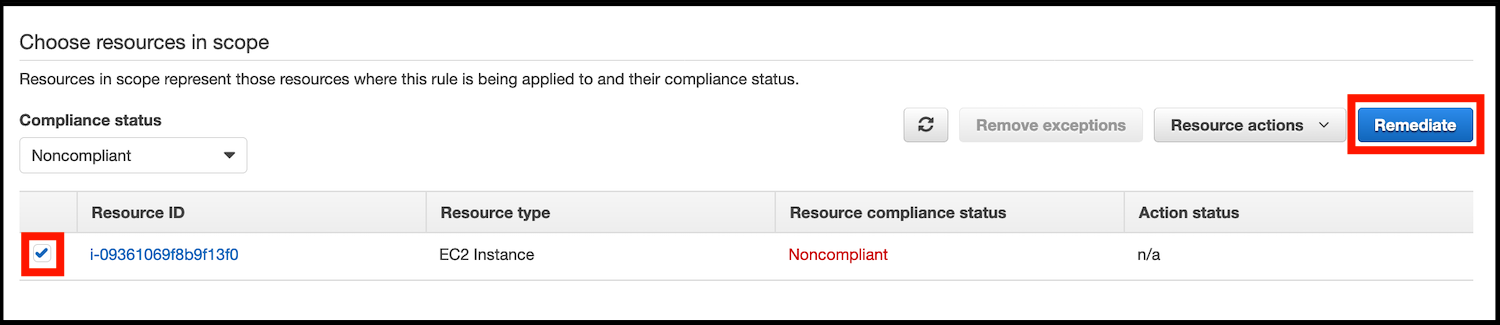
Click on the AWS Config rule name ec2-instance-managed-by-systems-manager and look at the non-compliant resource. Click on the selection box next to the EC2 instance you deployed earlier and then click on Remediate:
-
Open the AWS Systems Manager console and click on Automation in the left hand menu. You should see an Automation execution task listed that will attach an IAM role to the EC2 instance:
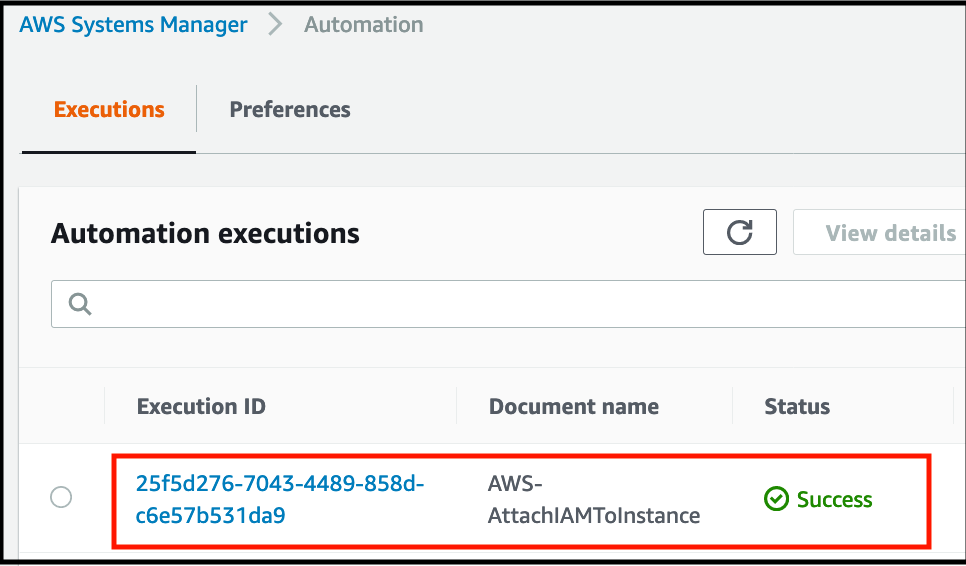
-
Restart the EC2 instance to quicken the process:
- Go to the EC2 Console
- Select the box next to your t3.large instance
- Click on the Actions button and choose Instance State, then choose Reboot.
- Click on the button Yes, Reboot.
-
Go back to the AWS Systems Manager console, and click on Managed Instances in the left hand menu. The EC2 instance should now be shown as a managed instance in the list (the deployed instance will have a blank Name field in the list). This step may take up to two minutes.
-
Go back to the AWS Config console and click on Rules.
-
Click on the rule name ec2-instance-managed-by-systems-manager.
-
The EC2 instance will no longer be displayed in the non-compliant list. Change the Compliance Status selection to Compliant and observe that the EC2 instance is now listed there.
KEY CONCEPT: What did we learn?
- How to create an AWS Config Rule to evaluate if instances are managed by SSM
- Importance of having the right IAM Role assigned for the instance to report to SSM.
- How to use AWS Systems Manager Automation documents to remediate non-compliant Instances.
Congratulations! You’ve now completed Lab 2!
Stuck? Watch this
This video has no audio