2. Evaluate Session Manager Configuration
To begin our evaluation, we need to examine the default configuration and behavior of Session Manager and determine what is needed to meet the requirements given to us for this project.
Evaluate cross-platform behavior, security context and default privilege levels
- Under Instances & Nodes in the AWS Systems Manager navigation menu, browse to the Managed Instances console.
- Select the session-manager-linux-prod instance, click Actions, click Start Session.
- Now that we have established an interactive shell to the instance, let’s determine our user context on the instance and evaluate our privilege level. Click into the Session Manager Console to be able to enter commands below:
- Execute
whoamito determine what user context we’re running under. - Execute
sudo sufollowed bycat /etc/sudoers.d/ssm-agent-usersto evaluate the privilege level assigned to the user ssm-user.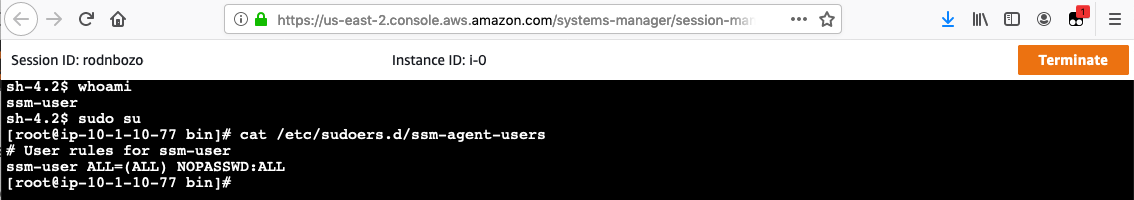
- Execute
- AWS Systems Manager works by having the SSM agent on the instance establish an outbound session to the Systems Manager service.
- Execute
netstat -nputw | grep -i ssmto validate this behavior and verify communications are actually being sent over a secure channel.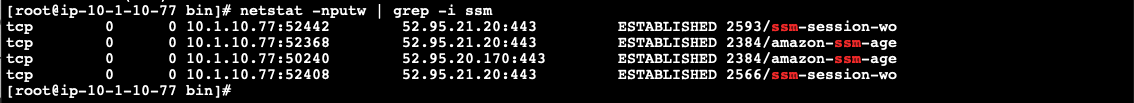
- Execute
- Click Terminate to terminate the session or type
exitand select close .
. - Select the session-manager-windows-prod instance, click Actions, click Start Session.
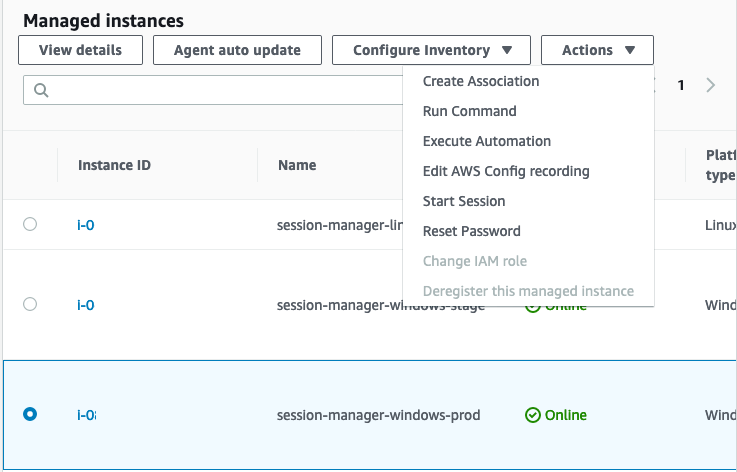
- Since this is a Windows instance, notice we’ve established an interactive PowerShell session.
- Execute
whoamito determine what user context we’re running under. - Execute
net user ssm-userto determine the local group memberships assigned to the local user ssm-user.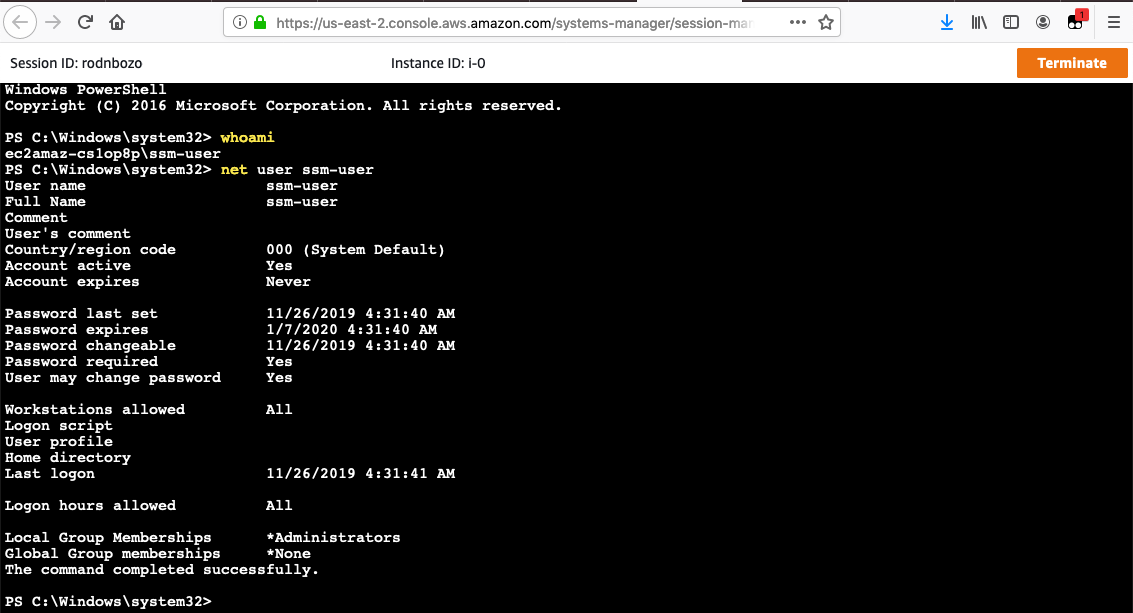
- Execute
- Click Terminate to terminate the session or type
exitand select close.
Evaluate the default auditing and logging configuration for Session Manager
- Under Instances & Nodes in the AWS Systems Manager navigation menu, browse to the Session Manager console.
- Select the Session history tab and review the session history details available.
 Note: that no information is presented under the Output location field.
Note: that no information is presented under the Output location field. 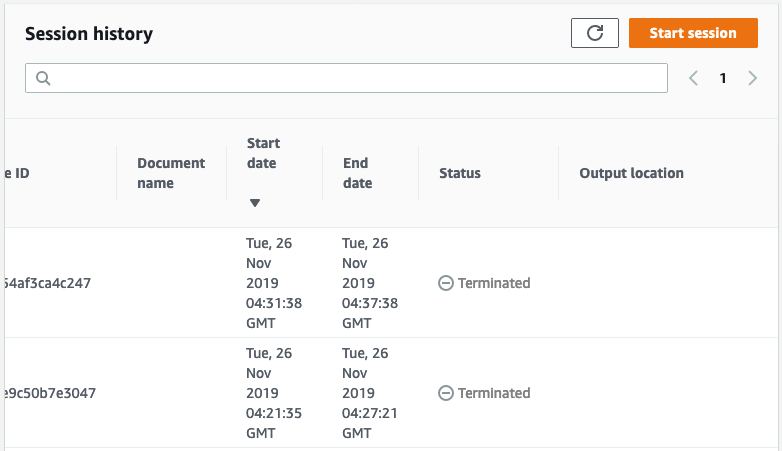
Evaluate the port requirements and default permissions of managed IAM policies
- Browse to the EC2 Instances console
- Click on any instance with its name starting with “session-manager".
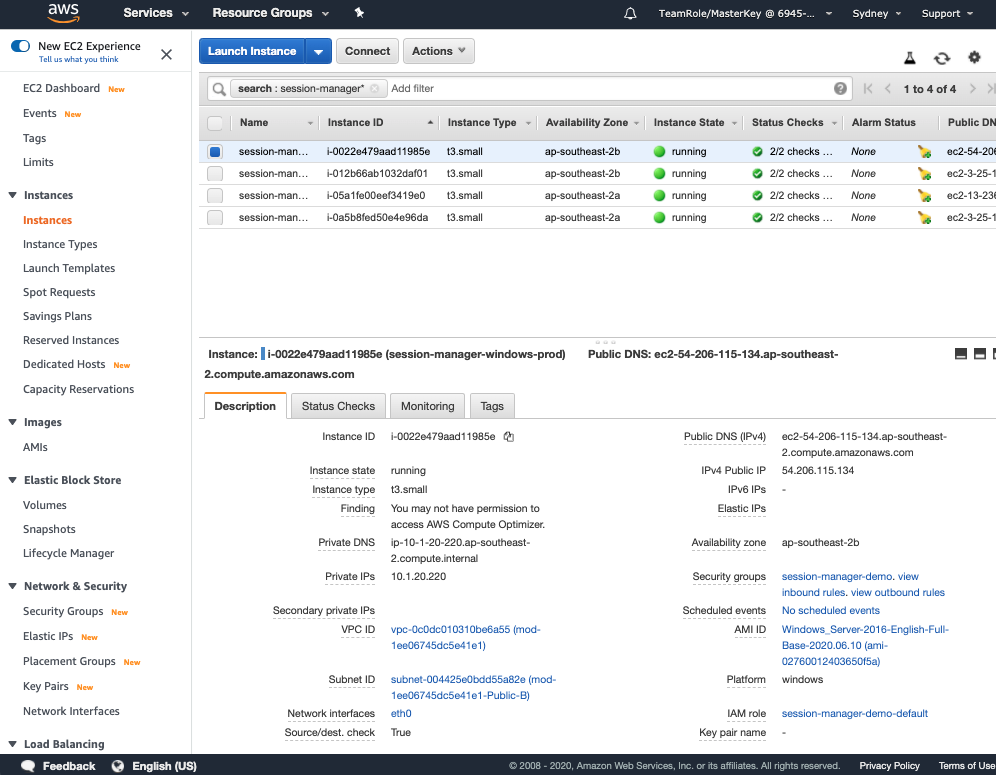
- In the pane to the bottom right under the Description pane, click on the session-manager-demo Security Group.
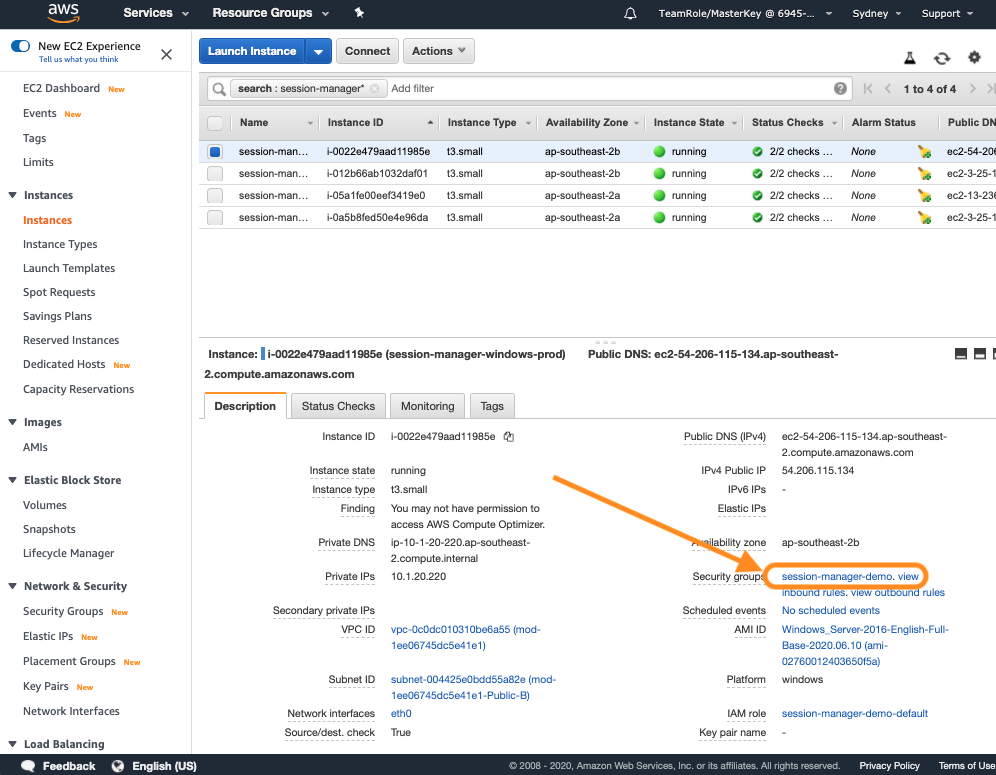
- Select the Inbound rules and Outbounds rules tab to evaluate the Security Group rules. You should notice that no inbound ports have been authorized and all outbound traffic is authorized.
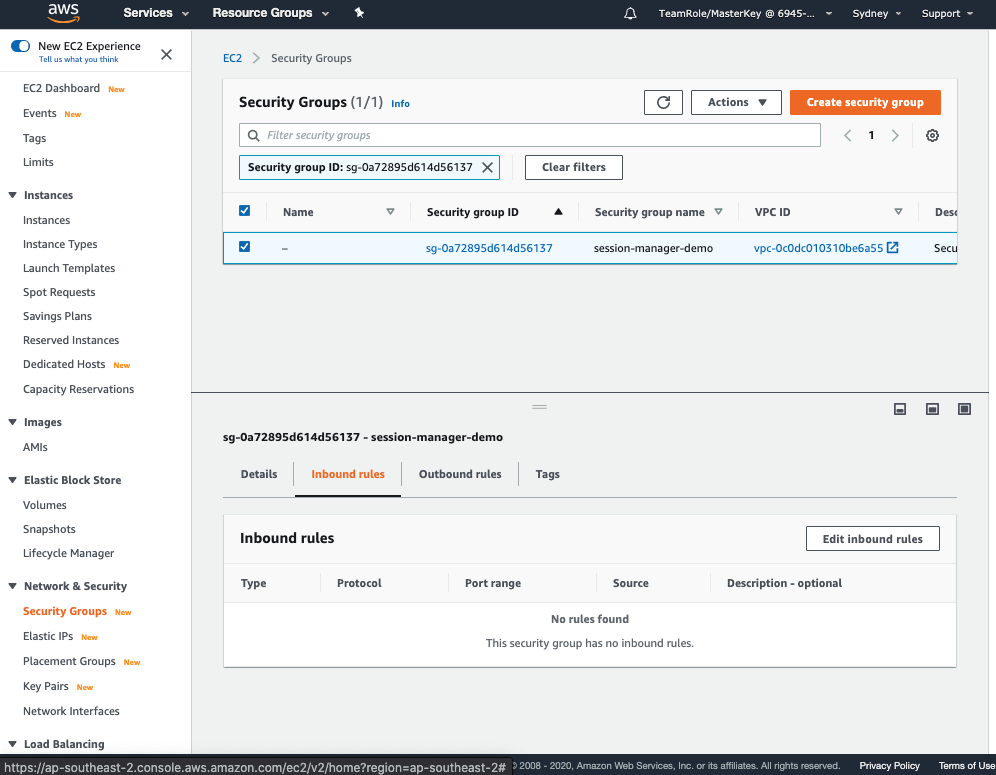
-
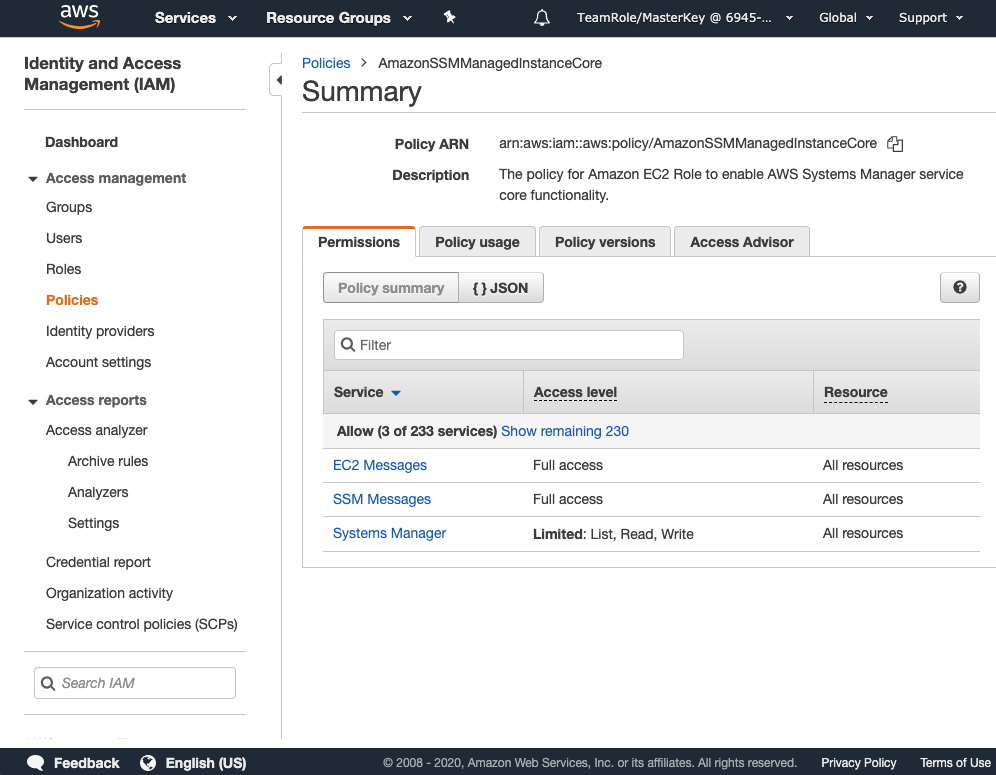
Lets now review the permissions granted by the managed IAM policy. Browse to the IAM console and under Policies click on AmazonSSMManagedInstanceCore. Note the permissions granted as shown in the image below.
This managed policy is attached to the session-manager-demo-default IAM role currently associated with our managed instances which can be seen under the Policy usage tab.
Stuck? Watch this
This video has no audio